Researchers presented the Mice-E-Mouse attack for eavesdropping on users with a gaming mouse
Researchers at the University of California, Irvine presented the Mic-E-Mouse attack, which allows gaming mice to be used for eavesdropping on users. The attack exploits a critical vulnerability in high-performance optical sensors in mice.

Attackers can use the polling rate and sensitivity of sensors to capture vibrations and convert them into audio data. The collected signal has low quality and other issues. Mic-E-Mouse involves sequential signal processing methods using machine learning to solve these problems and obtain an intelligible reconstruction of the user's speech.
In their research, the group used a standard mouse, and the VCTK and AudioMNIST speech datasets. They were able to increase the signal-to-interference-plus-noise ratio (SI-SNR) by 19 dB, the speaker recognition accuracy in automated tests by 80%, and in human tests for identifying information from the reconstructed recording, the Word Error Rate (WER) was 16.79%.
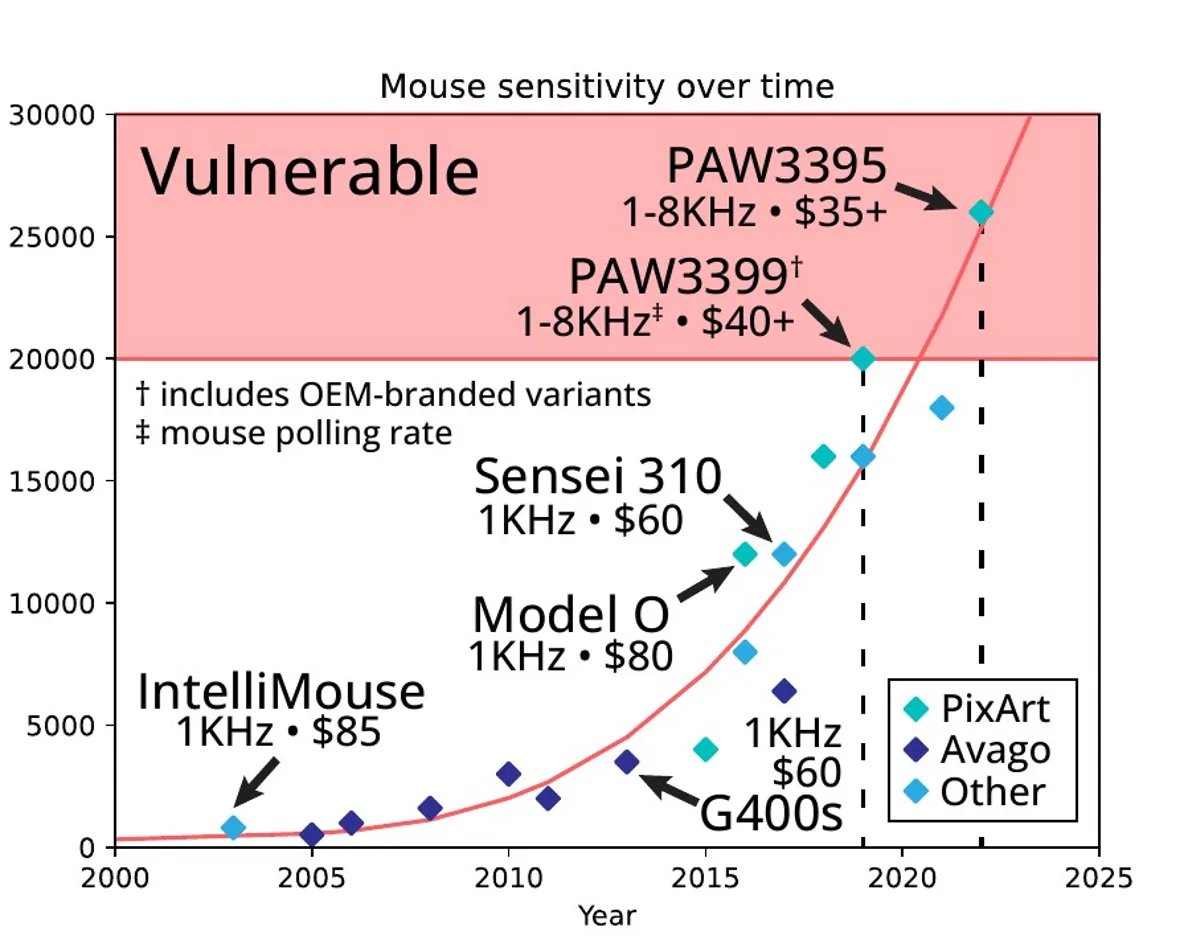
Researchers note that the availability of these mice, costing less than $50, is steadily increasing. As technological processes and sensor development improve, a further reduction in the price of such peripherals can be expected, the university believes, warning of an expanding attack surface.
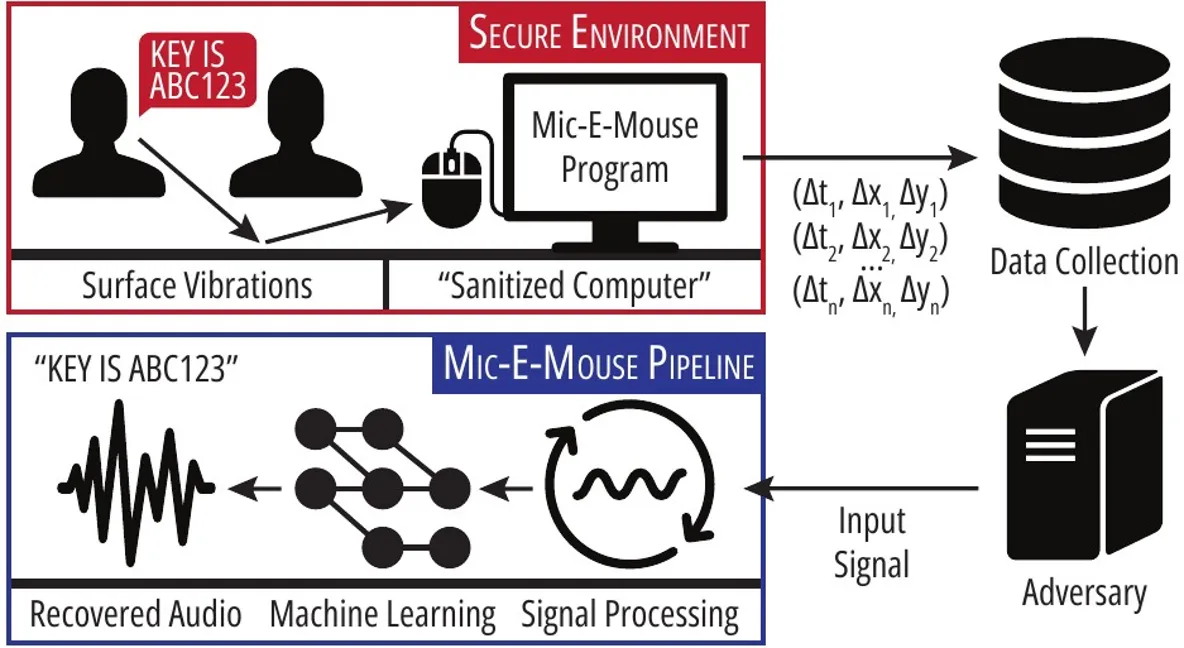
By exploiting the vulnerability with compromised or harmless (in the case of a web attack) software installed, it's possible to collect mouse data and extract audio signals. The software scheme is invisible to the average user during the data collection process. After this stage, all signal processing and data analysis can be performed remotely at any time at the attacker's initiative.
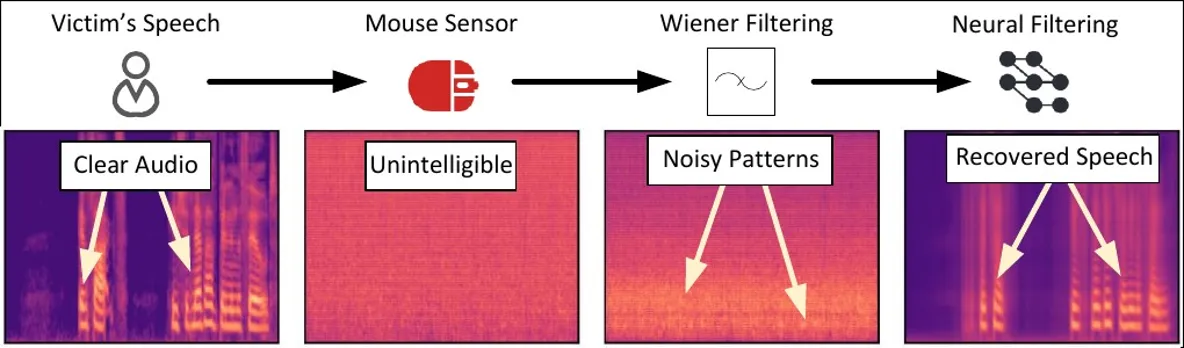
Researchers consider video games and other high-performance software as ideal targets for deploying the exploit. Many games contain network code that can be reused by the exploit without arousing suspicion.
The solution overcomes significant obstacles to obtain an understandable output signal. Mice with sensors having a resolution of 20,000 dots per inch (DPI) or higher are most vulnerable to Mic-E-Mouse.